Understand financial risks and discover essential technical and non-technical strategies to safeguard your company.
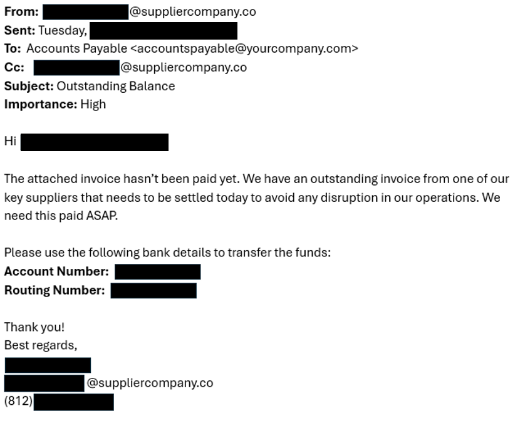
This email may look familiar to you. You may recognize the company name, the contact person, or their email address. You might have even had recent conversations and submitted payment for this exact invoice! So why are you now being contacted to pay again? Let’s dig into what Business Email Compromise (BEC) is and what you and your business need to know to protect your company from being scammed from your hard-earned income.
Business Email Compromise (BEC) is a type of email-based phishing attack that attempts to defraud a company. In a common scenario, an attacker gathers information on a target and attempts to gain access to their target’s or a supplier of the target’s email system. Once the attacker gains access, they will monitor the email system(s) to look for patterns of invoice payments. The attacker will then pose as a trusted party and interact with their target by asking for information, sending fake invoices, or asking for money to be sent using a new payment method. They even try to hide communications from real contacts with email rules that hide or delete legitimate email messages.
Most of the time, these fraudulent emails are caught, either by some security tool or a savvy accounts payable department. Sometimes however, these attacks are so compelling that the attacker will get paid. According to the FBI’s Internet Crime Complaint Center (IC3), 21,489 BEC complaints were received with adjusted losses over $2.9 billion USD in 2023 alone. Let’s discuss some ways that your company can protect itself from these attacks. Below, we will look at some technical controls and business processes that can be put into place.
Technical Security Controls
- Multifactor Authentication (MFA) can help protect against account compromise by requiring an additional verification form beyond username and password. MFA can stop authentication attacks even if login credentials are compromised.
- Email security solutions can detect and block phishing attempts before the email reaches an inbox, preventing users from even seeing these phishing messages. Some email security solutions can even warn users about suspicious wording in messages and first-time senders.
- Security Information and Event Management (SIEM) or Managed Detection and Response (MDR) systems continuously monitor and analyze security events. They provide real-time insights and alerts, enabling quick response to potential threats.
Non-Technical Business Processes
- Regular cybersecurity awareness training for all employees, including new hires, is vital. This training should cover basic security concepts such as phishing, BEC, and password security. Fostering an internal culture of security and cyber awareness can significantly reduce the risk of successful BEC attacks.
- Vendor management lists that include all key contact information and agreed upon secondary communication channels should be maintained. Employees should be encouraged to verify any unusual or unexpected requests through a secondary communication method, such as a phone call.
- Separation of duties can help protect against both internal and external risks by requiring whoever prepares the payable or writes the check to be different from the person that signs and approves it. If payments are over a certain predetermined amount, consider requiring a second signature from an approved signer.
- Regular reviews of business processes can help ensure that processes are being followed and are still working for the company.
By integrating both technical and non-technical measures, your business can establish a thorough defense strategy against business email compromise. Consistent implementation and review of these controls will aid in safeguarding business profits and ensuring a secure operating environment. If you’d like to learn more about Business Email Compromise defense strategies or would like an assessment of your systems, please contact your Keller Schroeder Select Account Manager to find out how our Information Security Team can assist.
References:
Arctic Wolf “Defending Against Business Email Compromise” Defending Against Business Email Compromise | Arctic Wolf
Arctic Wolf “The State of Cybersecurity: 2024 Trends Reports” The State of Cybersecurity: 2024 Trends Report | Arctic Wolf
Written By:

Tyler Carlisle
Practice Lead – Security Operations
Infrastructure Solutions Group
If you need any assistance with understanding the details within the advisory, understanding your current cybersecurity posture, your preparedness for a breach, or any other cybersecurity topic, we would love to have a discussion with you. Contact us today, and let’s chat about your environment and ways to lower your chances of becoming a victim of cybercrime.