Brad Mathis – [Senior Consultant – Information Security]
Brad Mathis – [Senior Consultant – Information Security]
Imagine the following scenario.
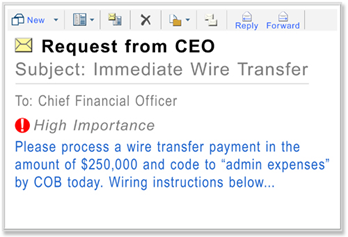
You are going through your daily routine and you receive an urgent email from the CEO. The email is urgent, appears to be time sensitive, and is requiring you to act immediately. You are aware the CEO is currently out on vacation or away on business, and is therefore unreachable. However, the email is direct and to the point. “Get this Done!” The email is asking for you, a member of the financial team, to process a payment or monetary transfer. It may even inform you someone from another company will be reaching out to you with further instructions, such as account numbers and routing information. An abbreviated example of such an email may look something like this:
What if you also received an email ahead of this one from someone in finance saying “Keep an eye out for an email from the CEO asking about a funds transfer”, followed by an email from the alleged company the CEO mentioned in their original email? Transferring large sums of money from one account to another is a normal part of your job. Although this chain of events is a bit out of the ordinary, it also seems perfectly legitimate. Would you process the transfer? Would a co-worker?
Sadly, far too many organizations are falling victim to these type of crimes known as CEO Fraud and Business Email Compromise (BEC). Some of the email senders’ email accounts are spoofed, meaning the criminal sender is making the recipient think the email is from the actual sender. Even more concerning is when the actual senders’ email account credentials are compromised and the criminal is able to send emails directly from the account of a CEO, CFO, Attorney, and so on. This may sound complicated, but it isn’t. With the advancement of malware laced email attachments and infected links, it is far too easy to install malicious software on a victim’s workstation, thereby allowing the criminal to capture every keystroke the legitimate user types. Even more concerning, cameras and microphones can be controlled by the criminals.
The FBI estimates the organizational amount lost to Business Email Compromise between October 2013 and February 2016 to be $2.3 Billion. Since January 2015, the FBI has seen a 270 percent increase in identified victims and exposed loss! Keep in mind, this is only the amount of loss actually reported. Many businesses remain quiet and never report their losses for fear of public reputation damage.
 Luckily, the risk of becoming a victim to this type of crime, as well as other email and web based threats can be reduced. A modern and evolving layered security infrastructure is extremely important. It cannot and should not be overlooked. However, the most effective and most overlooked method to reduce your risk of becoming a cybercrime victim is effective and measurable End User Security Awareness Education.
Luckily, the risk of becoming a victim to this type of crime, as well as other email and web based threats can be reduced. A modern and evolving layered security infrastructure is extremely important. It cannot and should not be overlooked. However, the most effective and most overlooked method to reduce your risk of becoming a cybercrime victim is effective and measurable End User Security Awareness Education.
While we constantly stress the importance of Vulnerability and Patch Management, this does not just apply to your technology. User vulnerability levels need to be assessed in order to gauge their likelihood of falling prey to a Phishing email and other criminal scams. This activity is most effective when supplemented with required security awareness training. This is where it sometimes gets tricky. The simulated phishing campaigns and security awareness training requirements must apply to ALL employees, up to and including the President and CEO.
Identifying your employee vulnerability baseline is an important and effective step toward lowering your overall risk profile, as well as empowering your workforce to always be on the lookout for malicious and criminal activity that can threaten your business.
So, Yes… It is OK to ignore the CEO’s request when it cannot be verified it is truly the request of the CEO. When the business is on the line, they will thank you for your due diligence.
How vulnerable are your users? How likely are they to fall prey to becoming a victim? How have you taken steps to get data to support your answers to those questions? When performing these employee vulnerability baseline assessments, we have already seen as high as a 75% failure rate for the initial Phishing test. Launching an effective awareness solution that allows you to measure risk and track improvements is a critical first step in lowering your employee vulnerability risk, making your organization less likely to become a victim of cybercrimes such as CEO Fraud, Business Email Compromise, and Ransomware.
Contact Keller Schroeder today to find out how we can help you implement solutions that effectively reduce your employee vulnerability risk through ongoing security awareness training and testing.